






Your Agentic AI Trust Layer
Unified identity, observability, and governance for every agent, tool, and action.











.svg)




AGENTIC AI SECURITY STARTS HERE
Secure your agentic AI ecosystem with hardware-bound identity. Gain complete visibility and control across every agent, identity, device, and action with the platform built for autonomous AI at scale.




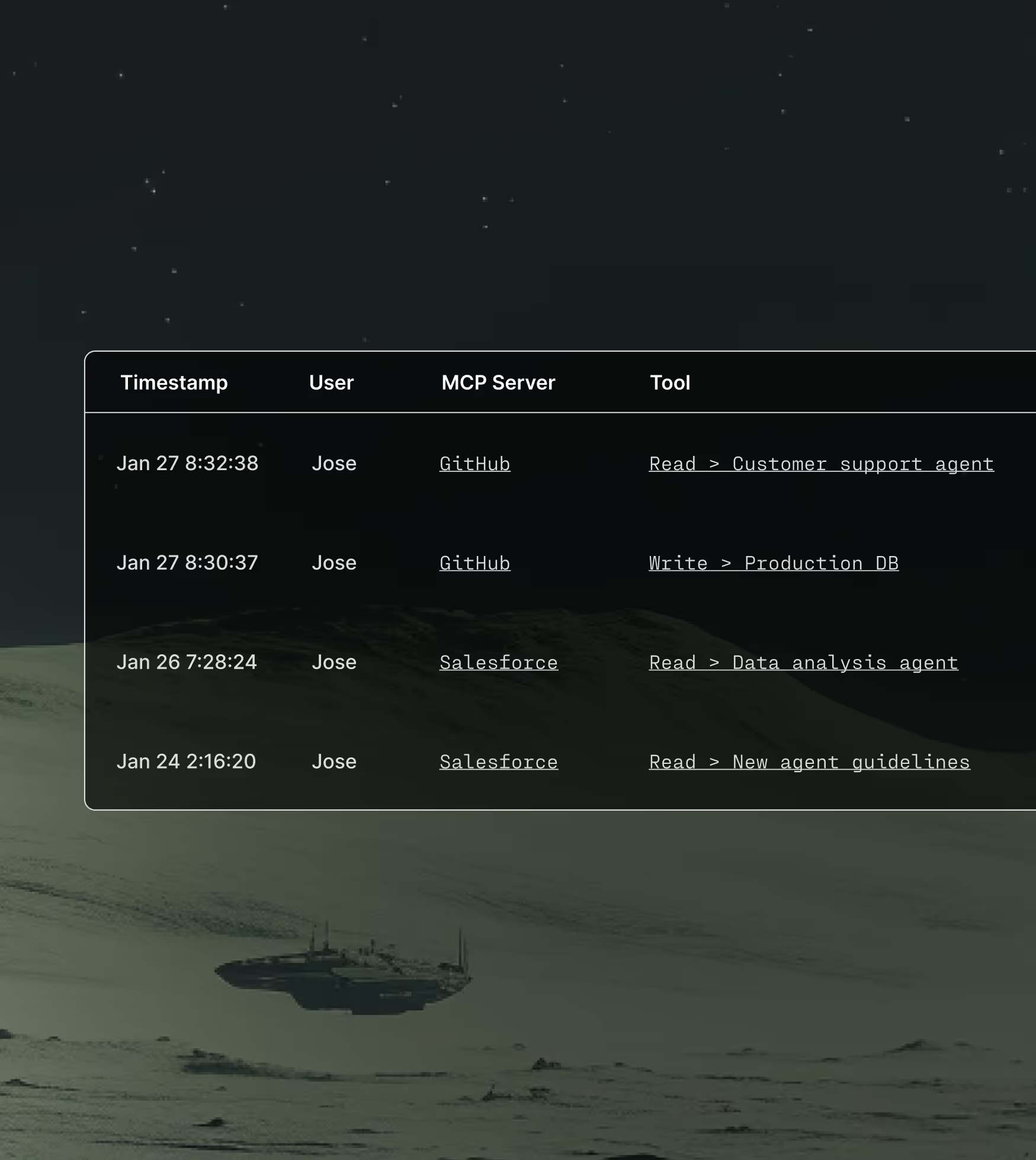
Full stack observability
Capture every LLM call, every MCP request, and every tool invocation. A complete audit trail for AI compliance, forensics, and real time monitoring.
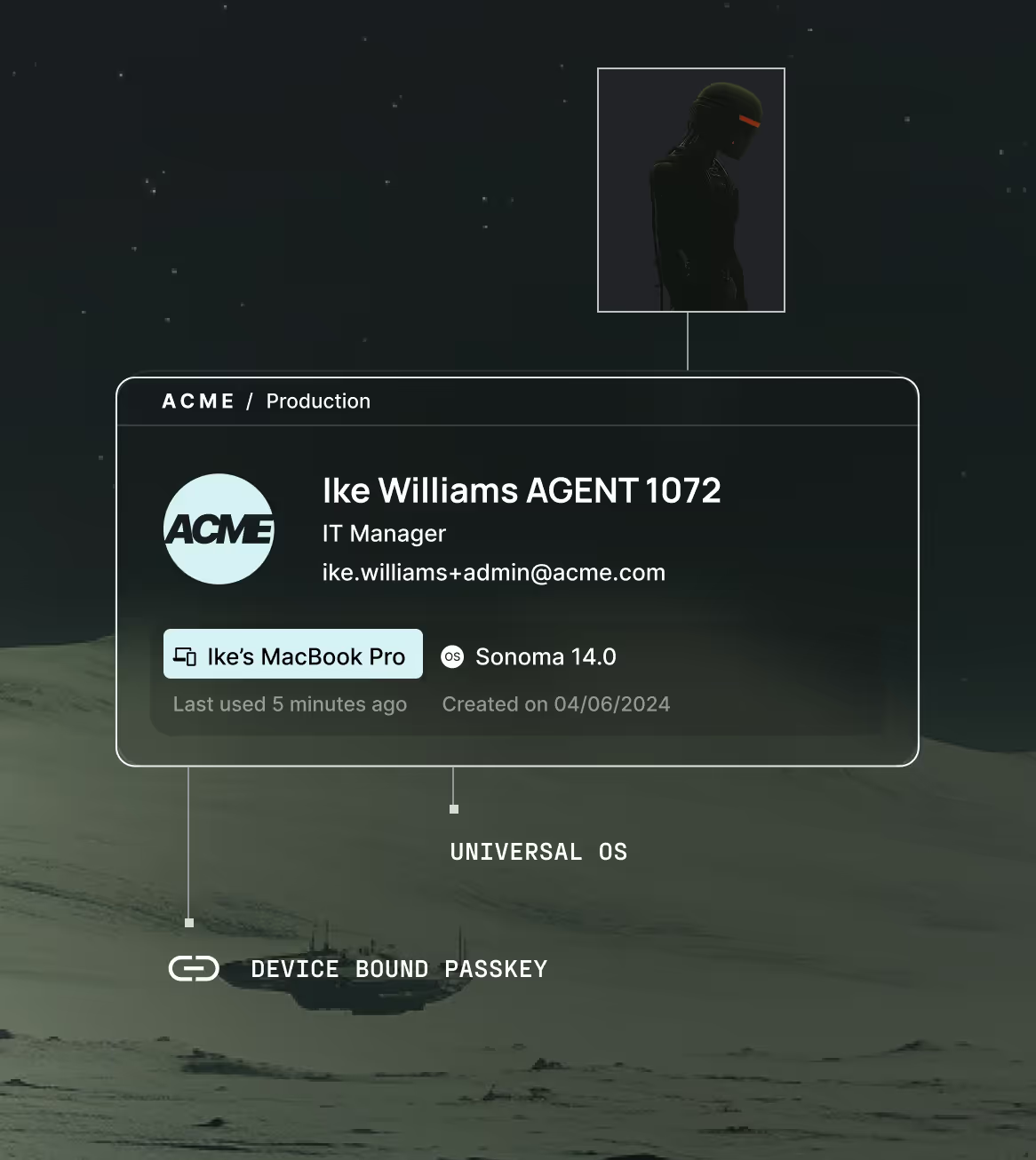
Hardware-bound agent identity
Give every AI agent a unique, verifiable, non-repudiable identity bound to the physical device it runs on. No shared secrets. No stealable credentials.
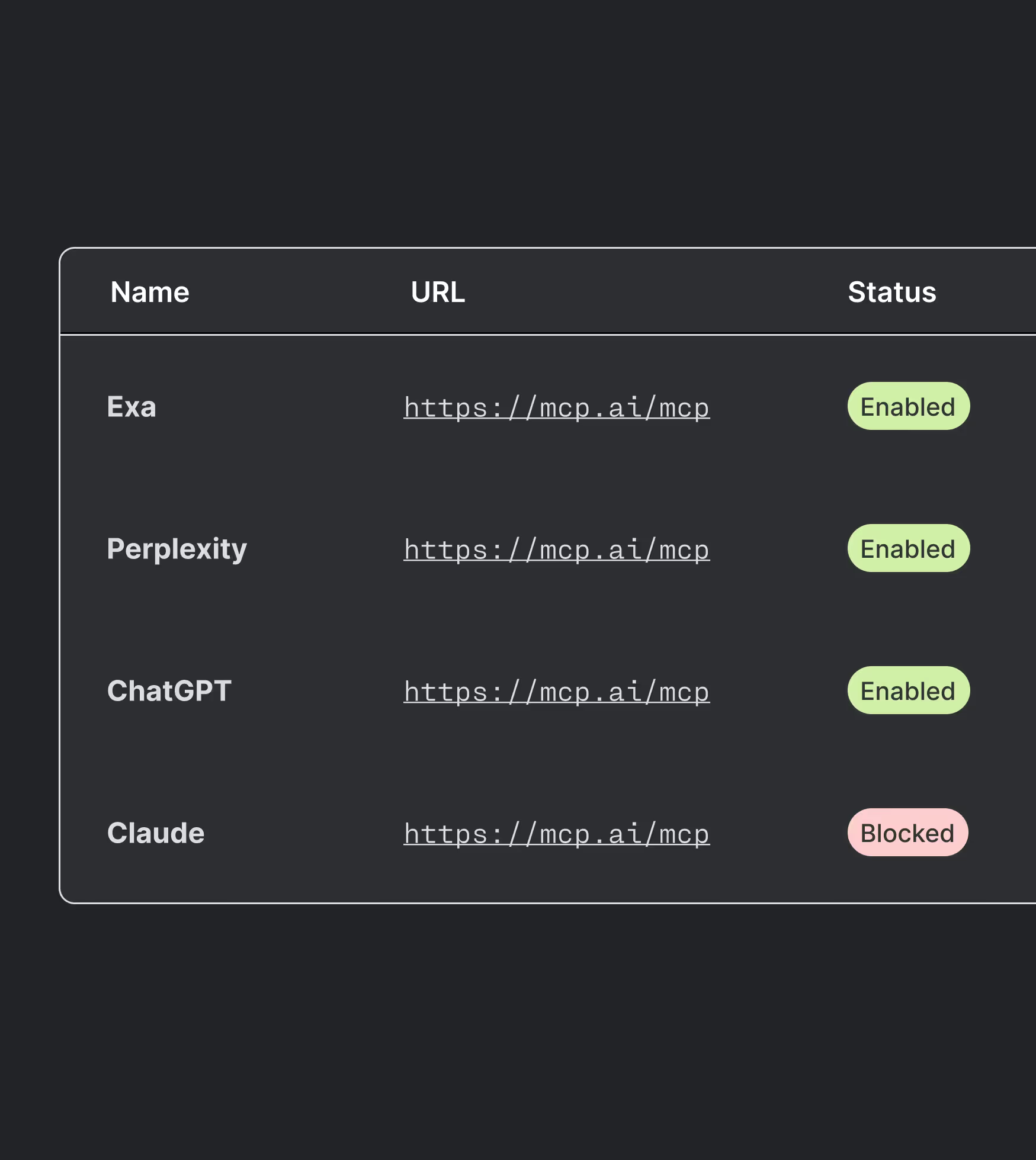
MCP governance
Discover every MCP server in your environment. Control which agents can access which tools, and enforce policies before actions execute.
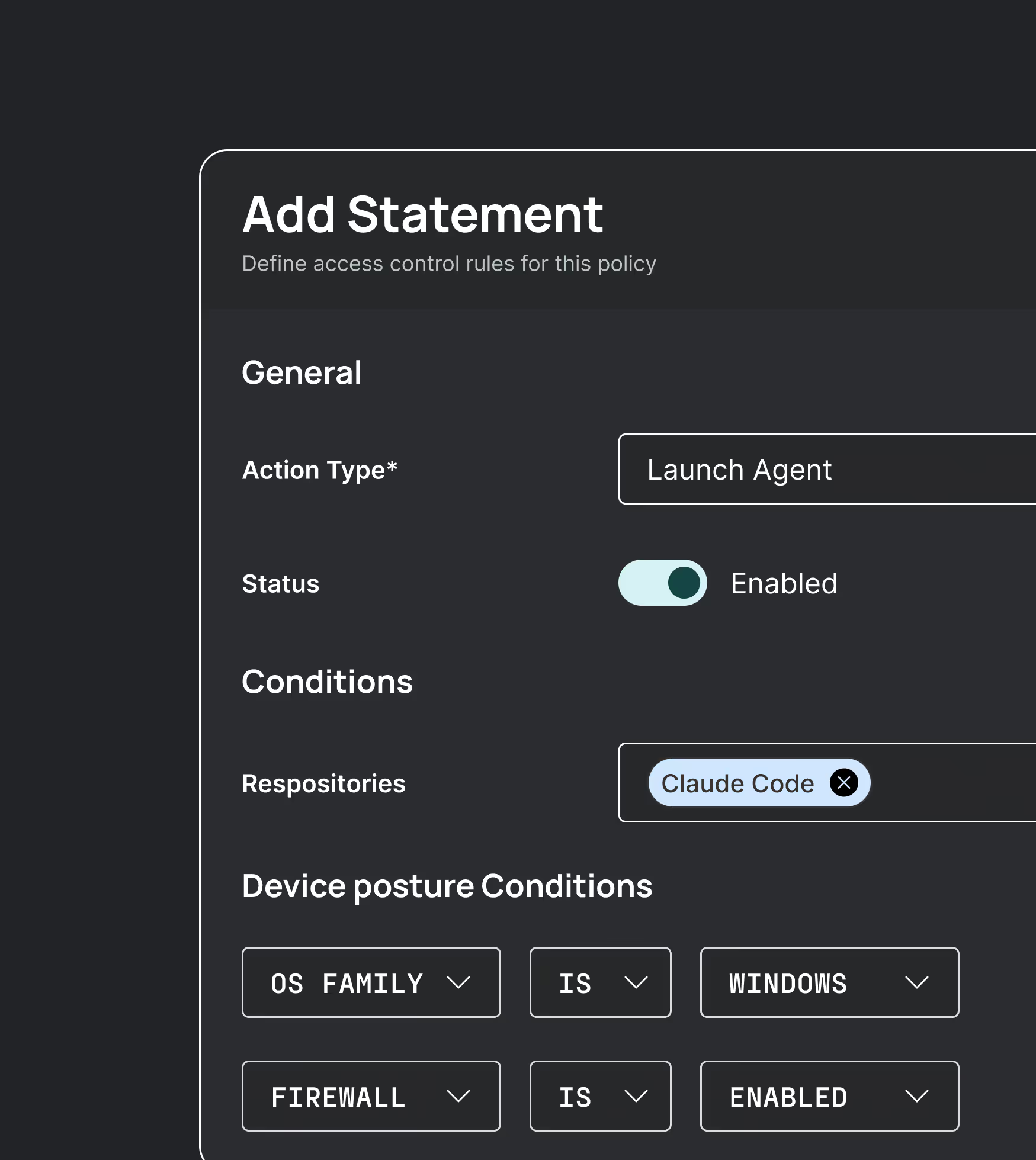
Policy enforcement
Log every prompt, every response, every tool call. Searchable, exportable, and ready for AI compliance reviews and incident response.
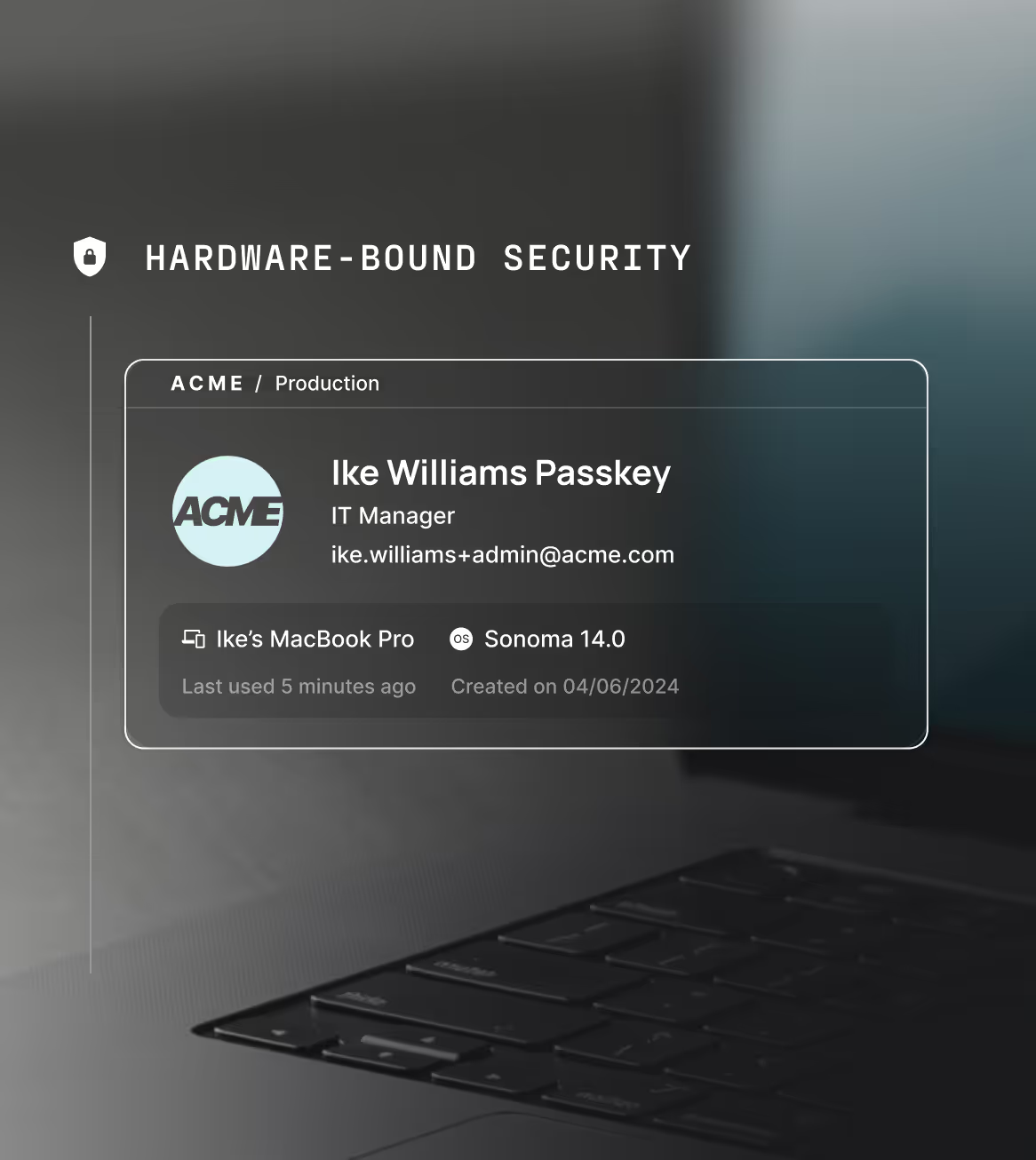
Eliminate API key sprawl
API keys are vaulted in hardware and never exposed. Stolen credentials are useless without the original device.
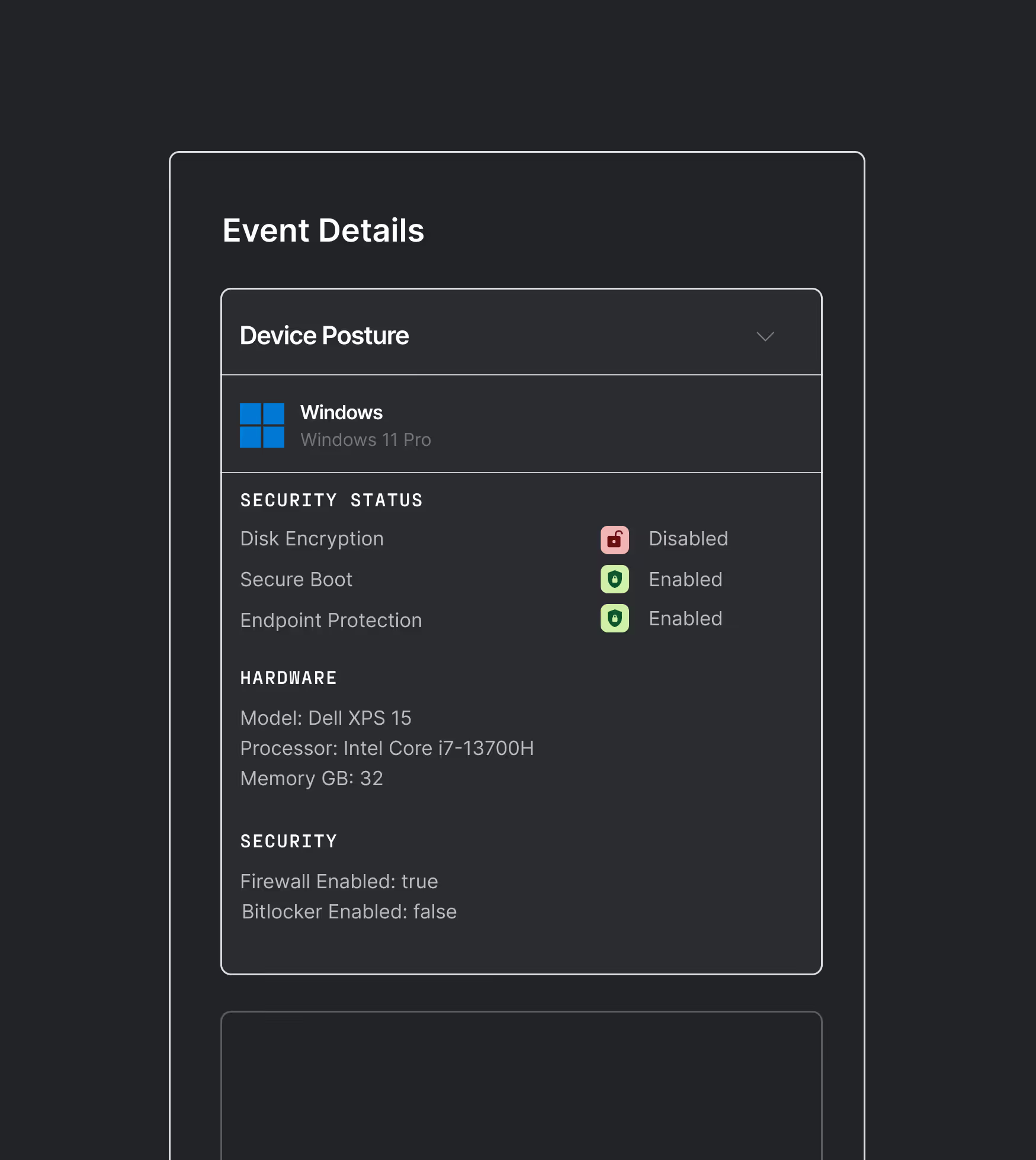
Complete device security visibility & enforcement
Verify device health continuously across managed and unmanaged devices before and during every session.
Control the identities you can't see or manage
One platform. One trust model. Extend the same cryptographic identity to your workforce and your non human identities.
Four critical threat vectors. Eliminated.
Credential theft and API key sprawl
AI agents rely on API keys scattered across code, config files, and developer machines. We vault credentials in hardware and inject them at runtime. Nothing to steal. Nothing to leak.
Unsanctioned agents
Users spin up agents without security review. We discover every agent in your environment automatically, sanctioned or not, and bring them under policy control.
Malicious MCP servers
Agents connect to external tools and services with no oversight.
We map every MCP server, enforce which agents can access which tools, log every invocation, and control what tools and MCP servers are allowed.
Unattributable agent actions
When something goes wrong, you cannot trace it back to a person. We tie every agent action to a verified human identity and a specific device, creating an unbreakable chain of accountability.



%20(1).avif)