Control Your Entire AI Ecosystem
From prompt to production: monitor, secure, and control all AI agents across your organization
Comprehensive AI security architecture
TOOL DISCOVERY
Explore and analyze AI tools available in your environment. Our discovery engine automatically catalogs every tool, tracks their capabilities, monitors their status, and provides comprehensive insights into your AI tool ecosystem.
AGENT DISCOVERY
Monitor and analyze AI agents connecting to your proxy. Automatically discover all agents in your environment, track their versions and types, analyze their behavior patterns, and maintain a complete inventory of your AI workforce.
TOOL EXECUTIONS
Monitor tool executions with full identity and agent context. Track every tool invocation in real-time, analyze execution patterns, identify anomalies, and maintain comprehensive audit trails for compliance and security.
GRAPH VIEW
Visualize relationships between identities, agents, and tools. Our interactive graph view maps your entire AI ecosystem, showing connections, dependencies, and data flows. Identify security risks and optimize your AI infrastructure.
MCP SERVERS
Manage Model Context Protocol servers for cloud-hosted tool execution. Monitor server status, track available tools, analyze performance metrics, and ensure secure communication between agents and external services.
ACTIVITY LOGS
View and analyze all API requests with detailed logging and audit trails. Search through comprehensive logs, filter by user or agent, track request patterns, and maintain complete visibility into all AI operations for security and compliance.
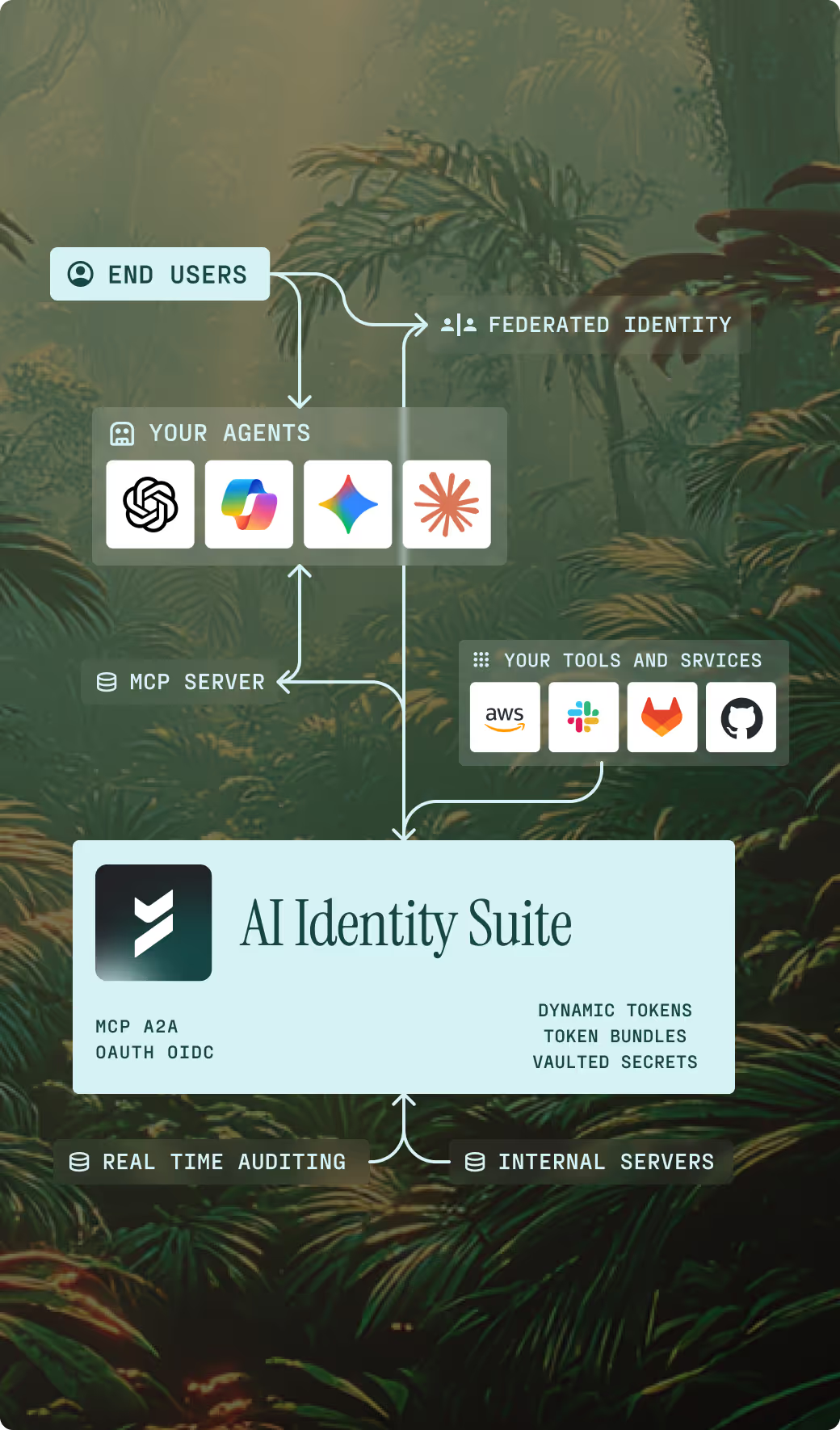
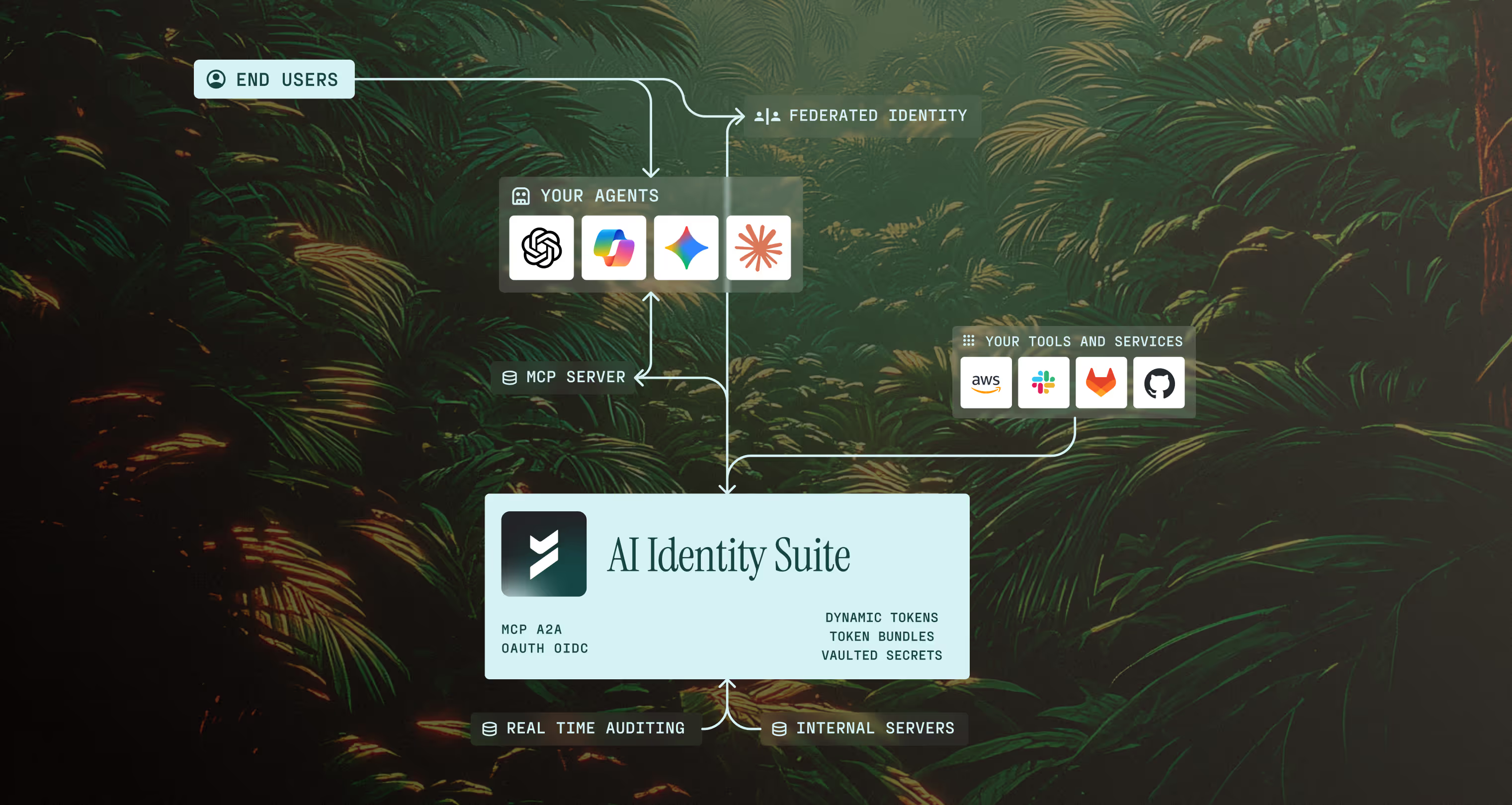
Deploy the AI Identity Suite
Install our lightweight agent across your infrastructure. The suite integrates seamlessly with your existing systems, requiring minimal configuration. Our deployment process is designed to be non-intrusive and can be completed in minutes.
Automatic Discovery
Once deployed, the AI Identity Suite automatically discovers all AI tools and agents in your environment. Our intelligent discovery engine maps your entire AI ecosystem, identifying connections, dependencies, and potential security risks.
Monitor and Analyze
Gain real-time visibility into all AI operations. Track tool executions, monitor agent behavior, and analyze patterns through our intuitive dashboard. Receive alerts for anomalies and potential security threats.
Secure and Comply
Enforce security policies, maintain compliance, and respond to incidents with comprehensive audit trails. Our platform provides the tools you need to secure your AI infrastructure and meet regulatory requirements.
.avif)

